After having in Part 5 configure part of Microsoft Exchange Server, in Part 6 and final part we will continue with Exchange Server configuration based migrations to Office 365 or more precisely Exchange Online, we ran the Exchange 2010 SP3 hybrid configuration wizard in order to set up the basic Exchange hybrid configuration.
Let’s go.…
Look at Current Hybrid Configuration
Let’s take a look at the stuff that was created behind the scene, when we ran the Hybrid Configuration Wizard (HCW).
Let’s first look at the hybrid configuration object itself. We can do so by launching the Exchange Management Shell (EMS), and run the following command: Get-HybridConfiguration

As you can see above, the settings (such as hybrid Client Access and Hub transport server, on premise smart host and federation domains) you specified when we ran the wizard have been set on the hybrid configuration object. But, this is not the only thing that have been configured. You can also see which features have been enabled (FreeBusy, MoveMailbox, MailTips, MessageTracking, OwaRedirection, OnlineArchive, SecureMail and CentralizedTransport), which are features we wish to enable between the on premise Exchange organization and the Exchange Online organization in Office 365.
In addition, the following has also been performed in the on premise Exchange organization:
A federation trust with the Microsoft Federation Gateway (MFG) has been established for the specified domain:

Creating a federation trust with the MFG is required in order to be able to set up an organizational relationship, which again is required in order to share free/busy information and calendars between the on premise Exchange organization and the Exchange Online organization in Office 365. With this said, it’s important to note that a trust isn’t set up with the MFG, instead the MFG merely acts as a trust broker between the involved Exchange organizations.
“tenant_name.mail.onmicrosoft.com” has been added as an accepted domain:

Adding the “tenant_name.mail.onmicrosoft.com” domain to the “Accepted Domains” list as an authoritative domain is required in order for the on premise Exchange organization to accept inbound e-mail messages destined for a mailbox user located in Exchange Online. When a mailbox is moved from the on premise Exchange organization to Exchange Online, the source mailbox user object is converted to a mail user object, which is configured with an external address of “alias@office365labdk.onmicrosoft.com“. We will look more at this later in this article series.
“tenant_name.mail.onmicrosoft.com” and “onprem.local” has been added as a remote domain:

A remote domain is an SMTP domain that is external to our Exchange organization. When a new remote domain is created, it’s possible to specify the remote domain is used for Exchange Online purposes. With a remote domain, we can configure out of office and message formatting settings. The HCW sets the ideal setting for a hybrid and enables the SMTP domain as the domain used for an Office 365 tenant, which is important in relation to provisioning of new remote mailbox users (users that get a mailbox created directly in Exchange Online).
The default E-Mail Address policy has been updated, so that it stamps a secondary proxy address (alias@tenant_name.mail.onmicrosoft.com) on mailbox user objects:

The SMTP address “alias@lacosanostra365.mail.onmicrosoft.com“ is added to the default E-mail address policy, so that it can be stamped as an additional proxy address on the mail objects in the organization. As mentioned earlier, when a mailbox is moved to Exchange Online, the source mailbox user object is converted to a mail user object and in order to be able to set “alias@office365labdk.mail.onmicrosoft.com“ as the external e-mail address, it must already be stamped on the object. The HCW also creates a receive connector on each of the hybrid servers. The purpose of this receive connector is to accept inbound mail that comes directly from Exchange Online in Office 365. The receive connector accepts anonymous connections secured using TLS, but only from the IP range used by Office 365.
In addition, the HCW will create a send connector that will route all e-mail messages destined for “tenant_name.mail.onmicrosoft.com” to Exchange Online in Office 365.

And finally, an organizational relationship has been established with the Exchange Online organization in Office 365:

The organization relationship is used to configure what kind of features should be enabled between the on premise Exchange organization and Exchange Online and for availability sharing at what level.
Let’s take a closer look at the organization relationship that has been created. We can do this by running the following command in the Exchange Management Shell (EMS): Get-OrganizationRelationship | fl
By default, free/busy is enabled with limited details. In addition, mailbox moves, delivery reports, MailTips and online archive are enabled. Moreover, a target OWA URL is specified and by default, it will be set to: “http://outlook.com/owa/tenant_name.onmicrosoft.com”. The target OWA URL is the URL that a user will be non-transparently redirected to (we will look at this later in this article series), when he tries to access his mailbox using the existing OWA namespace (i.e. http://mail.domain.com/owa) after his mailbox has been moved to Exchange Online. Lastly, a target autodisocver has been set by the HCW.
This is the endpoint used to reach out to the Exchange Online organization for the configured features, when a request comes from the on premise Exchange organization to the Exchange Online organization.
In Office 365, the following was configured, when we ran the HCW
Just like for the on premise Exchange organization, the domains used for routing between on premise and Exchange Online has been added as “Accepted Domains” in the Exchange Online organization.

Likewise, for remote domains, these have been configured in Exchange Online. An organization relationship has been configured in Exchange Online, so the sharing requests etc. from an Exchange Online mailbox user to an on premise mailbox user is sent to the on premise Exchange organization.

Just like is the case with the on premise Exchange organization, we can get additional information about the configuration of the organization relationship by running the following command: Get-OrganizationRelationship | fl
Update Hybrid Configuration
If you at some point wish to update the hybrid configuration in your environment, you can do so via the HCW or EMS.
If you want to use the HCW, you simply click on the hybrid configuration object in the EMC, and select “Manage Hybrid Configuration” in the context menu.

If you want to use EMS, you first set the required configuration using the Set-HybridConfiguration cmdlet and then you run the Update-HybridConfiguration cmdlet to push the new configuration to Office 365.
Read more about the Set-HybridConfiguration cmdlet here and the Update-HybridConfiguration cmdlet here.
That is we will move an on premise Exchange mailbox to Exchange Online and then we will test the browser and client behavior and see what to expect when a mailbox has been moved from on premise Exchange to Exchange Online. Moreover, we will be provisioning a new mailbox in Exchange Online using the “New Remote Mailbox” wizard and the “New-RemoteMailbox” cmdlet.
Lastly, I explain what to consider when it comes to decommissioning your Exchange on premise servers or just the legacy Exchange servers within your on premise environment.
Moving a Mailbox
Now that we have configured a hybrid deployment, let’s test things out to ensure they work as expected. First, we will move an on premise mailbox to Exchange Online using the “New Remote Move Request” wizard. This can be done by right-clicking on an on premise mailbox and selecting “New Remote Move Request” in the context menu as shown in

On the “Introduction” page, click “Next”.

On the “Connection Configurations” page, make sure “Target forest” is set to “the name you gave the additional Exchange forest”, then enter the FQDN for the Exchange hybrid server that has the Client Access server role installed. Also, enter the credentials for an on premise administrator and click “Next”.

On the “Move Settings” page, click “Browse” and then select the target delivery domain (in this case “office365labdk.mail.onmicrosoft.com”). Since, we’re moving a mailbox to Exchange Online, we cannot select the target database (it will be picked randomly). Click “Next”

On the “Configuration Summary” page, click “New” in order to create the remote move request in Exchange Online.

On the “Completion” page, click “Finish”

Let’s go and see how to migrate mailbox data by using the Exchange Admin Center in Office 365
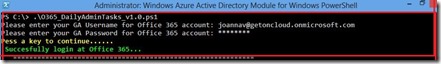
1. Sign in to the Office 365 portal (https://portal.microsoftonline.com).
2. Click Admin, and then click Exchange.
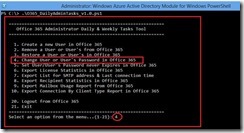
3. Click Migration, click New (+), and then click Onboarding.
4. Select the migration option that you want, and then click Next. Migration options are as follows:
· Remote move
· Staged migration
· Cutover migration
· IMAP
The following screen shot shows the migration options:

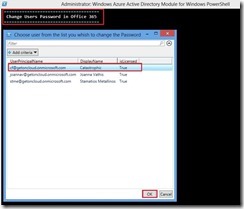
In New migration batch window, click New (+)

Select the user/s that you want to move and click add and then ok and Next


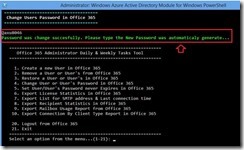
In the next window enter on premise account credentials and click Next

After the wizard finish, the mailbox will be moved successful to Office 365
Enjoy…

![clip_image001[4] clip_image001[4]](https://securitynebulaai.com/wp-content/uploads/2015/02/clip_image0014_thumb.jpg?w=330&h=191)
![clip_image002[4] clip_image002[4]](https://securitynebulaai.com/wp-content/uploads/2015/02/clip_image0024_thumb.jpg?w=371&h=132)
![clip_image003[4] clip_image003[4]](https://securitynebulaai.com/wp-content/uploads/2015/02/clip_image0034_thumb.jpg?w=401&h=78)
![clip_image004[4] clip_image004[4]](https://securitynebulaai.com/wp-content/uploads/2015/02/clip_image0044_thumb.jpg?w=469&h=198)
![clip_image005[5] clip_image005[5]](https://securitynebulaai.com/wp-content/uploads/2015/02/clip_image0055_thumb.jpg?w=549&h=58)
![clip_image006[5] clip_image006[5]](https://securitynebulaai.com/wp-content/uploads/2015/02/clip_image0065_thumb.jpg?w=558&h=166)
![clip_image007[5] clip_image007[5]](https://securitynebulaai.com/wp-content/uploads/2015/02/clip_image0075_thumb.jpg?w=558&h=92)
![clip_image008[6] clip_image008[6]](https://securitynebulaai.com/wp-content/uploads/2015/02/clip_image0086_thumb.jpg?w=558&h=115)
![clip_image009[4] clip_image009[4]](https://securitynebulaai.com/wp-content/uploads/2015/02/clip_image0094_thumb.jpg?w=558&h=177)
![clip_image010[4] clip_image010[4]](https://securitynebulaai.com/wp-content/uploads/2015/02/clip_image0104_thumb.jpg?w=313&h=464)
![clip_image011[5] clip_image011[5]](https://securitynebulaai.com/wp-content/uploads/2015/02/clip_image0115_thumb.jpg?w=558&h=106)
![clip_image012[4] clip_image012[4]](https://securitynebulaai.com/wp-content/uploads/2015/02/clip_image0124_thumb.jpg?w=558&h=80)
![clip_image013[4] clip_image013[4]](https://securitynebulaai.com/wp-content/uploads/2015/02/clip_image0134_thumb.jpg?w=510&h=219)